WireGuard VPN
Self-hosted WireGuard with a web UI for adding/removing peers, downloading configs, and viewing status.
Self-hosted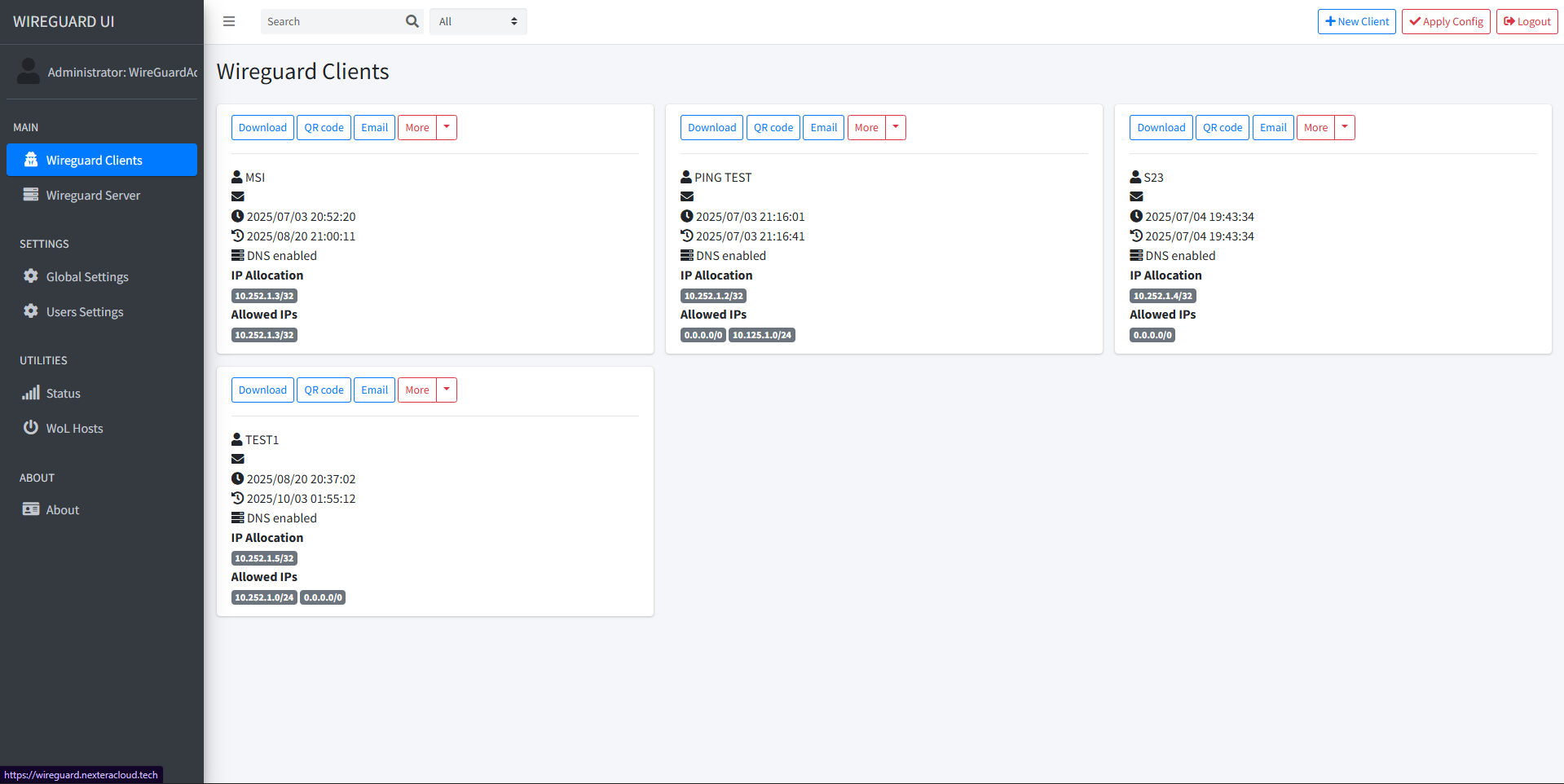
What I run
- WireGuard server on Linux with a lightweight web UI.
- Per-client IP allocation and allowed-IPs rules (split/full tunnel as needed).
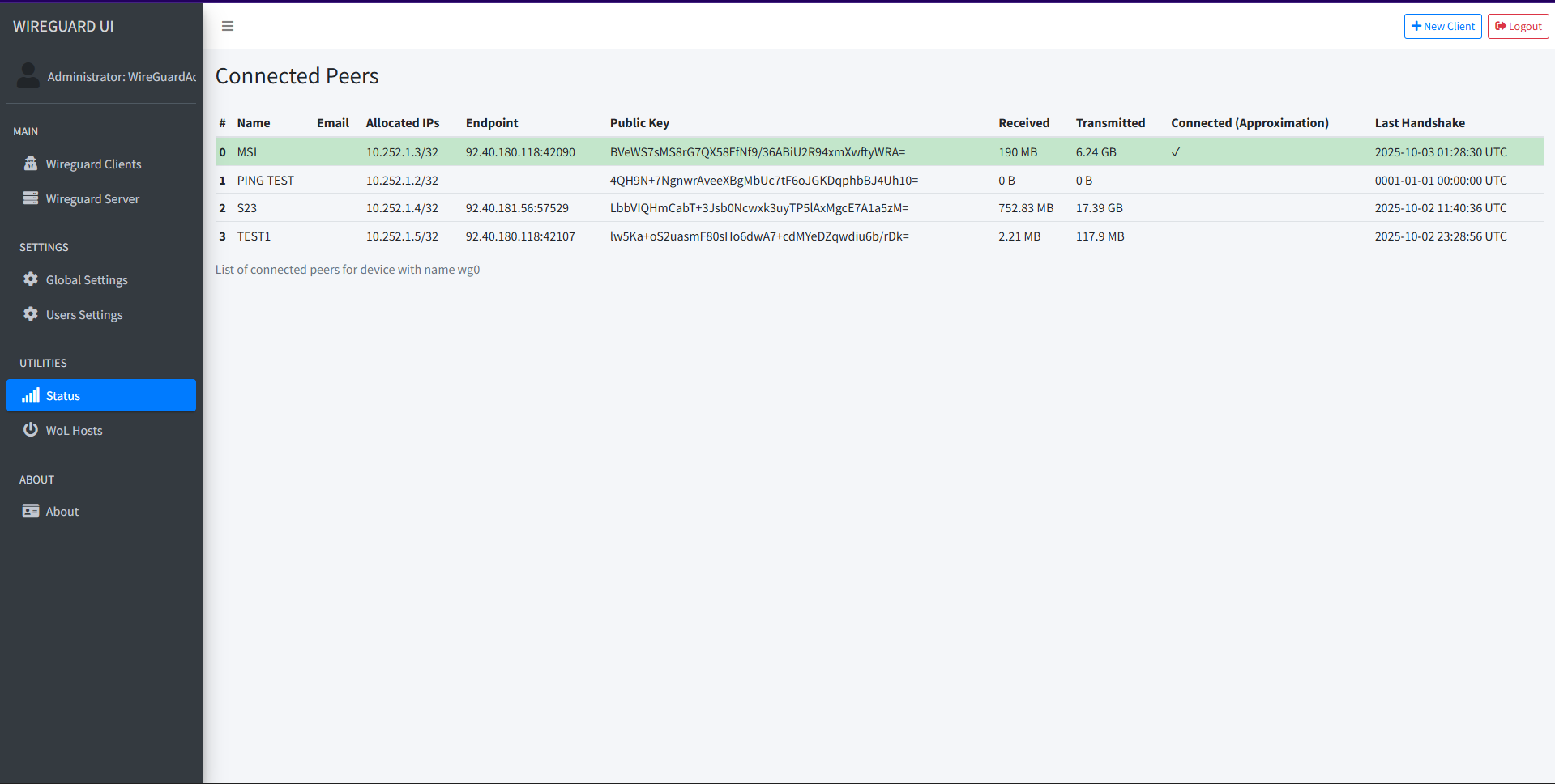
- Backups of server keys/config; UI provides per-peer QR and .conf.
- Ingress limited and monitored; certs automated.
Snippets
Install base WireGuard on Rocky/EL:
dnf install -y epel-release
dnf install -y wireguard-tools
# bring interface up once config exists:
# wg-quick up wg0Minimal /etc/wireguard/wg0.conf (server):
[Interface]
Address = 10.252.1.1/24
ListenPort = 51820
PrivateKey = <SERVER_PRIVATE_KEY>
# optional routing/NAT:
# PostUp = iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
# PostDown = iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
# example client
PublicKey = <CLIENT_PUBLIC_KEY>
AllowedIPs = 10.252.1.3/32Client config snippet:
[Interface]
PrivateKey = <CLIENT_PRIVATE_KEY>
Address = 10.252.1.3/32
DNS = 10.252.1.1
[Peer]
PublicKey = <SERVER_PUBLIC_KEY>
Endpoint = vpn.example.com:51820
AllowedIPs = 0.0.0.0/0, ::/0
PersistentKeepalive = 25Quick checks:
# show peers/handshakes quickly
wg show
# bring interface up/down
wg-quick up wg0
wg-quick down wg0I keep management in the web UI for speed (add/remove peers, rotate keys) and automate backups of configs.